Logs Are Back-and Other Takeaways from AWS re:Invent
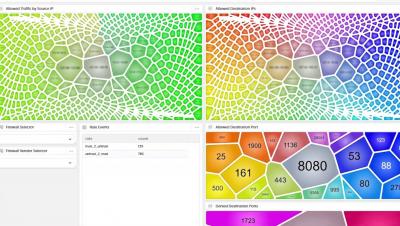
This month Devo exhibited at the AWS re:Invent conference in Las Vegas. I asked a few Devo colleagues who attended the show for their insights about what they heard and saw. Among the many visitors to the Devo booth there were a lot of similar questions about log management and related topics. “There were many log vendors at the show, so people wanted to hear what makes Devo unique,” said Seema Sheth-Voss, vice president, product marketing, for Devo.