Unmatched Coverage for Cloud and Hybrid Workloads: Sysdig's Next Generation Instrumentation
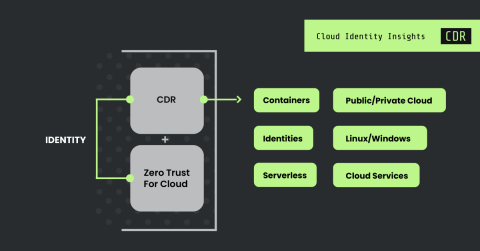
In today’s rapidly changing and evolving cloud-native environments, security and infrastructure teams face challenges ranging from managing complex deployments to ensuring capability across their entirety of their diverse infrastructure. EDR and XDR tools cannot provide comprehensive coverage of cloud workloads, making them fundamentally unsuited for cloud security.