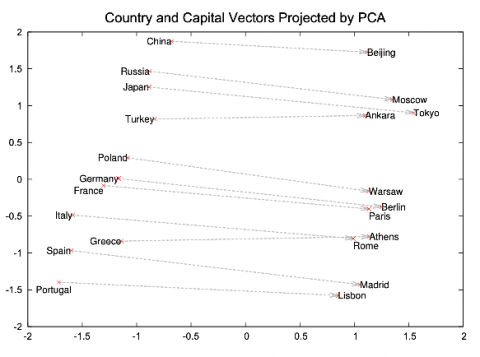
Here Comes TroubleGrabber: Stealing Credentials Through Discord
“TroubleGrabber” is a new credential stealer that is being spread through Discord attachments and uses Discord messages to communicate stolen credentials back to the attacker. While it bears some functional similarity to AnarchyGrabber, it is implemented differently and does not appear to be linked to the same group. TroubleGrabber is written by an individual named “Itroublve” and is currently used by multiple threat actors to target victims on Discord.