Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Hindsight 2020: Revisiting Netskope's Cybersecurity Predictions for the Year No One Saw Coming
2020, as a year, has been anything but predictable, but we’re proud to say we got even a few things right. Here’s a look back at some pretty big trends, a couple of things that sort of happened, and at least one big miss.
What is clickjacking and how can I prevent it?
Cyber attackers are continuously cultivating their methods to evade detection. Now, they can cloak a seemingly innocuous webpage with an invisible layer containing malicious links. This method of attack, known as clickjacking, could cause you to activate your webcam or transfer money from your bank account. In this post, we outline the different types of clickjacking attacks and teach you how to best defend yourself against this application security threat.
Myth Busting 101: Challenging stereotypes and grasping opportunities
Grow your Small Business with Workforce Intelligence
Did you know that collecting data regarding employee behaviors and patterns can help business owners create accurate, efficient business plans? Companies are using workforce intelligence to accurately and objectively build stronger internal organizations using big data. Workforce intelligence uses a combination of artificial intelligence, SaaS tools, analytics, and visual reporting to help employers oversee and manage employees more effectively.
Four requirements for open source vulnerability management in a DevOps environment
Most applications contain open source code, which can expose companies to risks if left unchecked. Make the most of your open source vulnerability management with the right approach and tooling.
7 High-Risk Events to Monitor Under GDPR: Lessons Learned from the ICO's BA Penalty Notice
Hello Security Ninjas, Today's IT world is complex and can be challenging for security operations teams. Nowadays, more apps are being integrated and interconnected than ever before. Cloud services and SaaS solutions purchased all throughout the organization outside of the IT department add even more complexity. Communicating to application and service owners the kind of activities that need to be logged and sent to the SOC can be a daunting task.
How to Handle a Data Breach Within Your Company
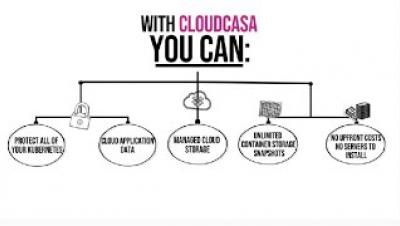
Introducing CloudCasa: Kubernetes Backup and Disaster Recovery
Securing Kubernetes clusters with Sysdig and Red Hat Advanced Cluster Management
In this blog, we introduce the new integration between Sysdig Secure and Red Hat® Advanced Cluster Management for Kubernetes that protects containers, Kubernetes, and cloud infrastructure with out-of-the-box policies based on the Falco open-source runtime security project. Organizations are quickly growing their Kubernetes footprint and need ways to achieve consistent management and security across clusters.