Nucleus Security Launches Nucleus Vulnerability Intelligence Platform to Accelerate Threat Assessment and Risk Mitigation
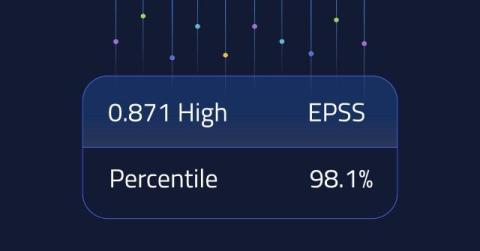
Nucleus Security announces the launch of its Nucleus Vulnerability Intelligence Platform. Nucleus Vulnerability Intelligence Platform enables enterprises to aggregate, analyze, and act on insights from government, open-source, and premium threat intelligence feeds while reducing manual effort, accelerating threat assessment, and promoting proactive remediation.