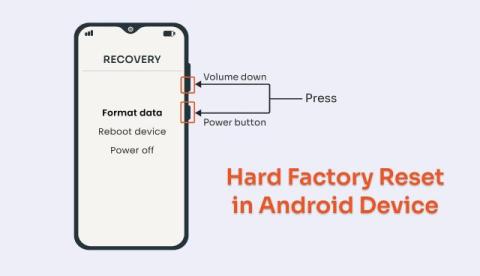
How to Prevent Factory Reset on Android Work Devices?
Keeping your Android work devices safe from unwanted factory resets is really important for businesses today. Let’s learn how Mobile Device Management (MDM) can help prevent the misuse of Android work devices from unauthorized hard and soft resets, making it an easy way to protect your data and keep everything working smoothly!