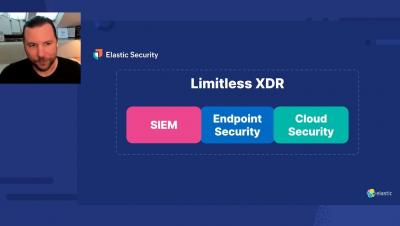
Elastic Security has introduced the industry’s only free and open Limitless XDR solution. Now, native endpoint security comes on every host, automated detections prioritize the biggest risks, and universal data ingestion and centralized analysis accelerate analyst workflows across triage, investigation, escalation, and response. Join our keynote session to learn what unrestricted data ingestion, visibility, and analysis means for analysts, the impacts that key technology and cloud integrations have on security teams, and what the future with Limitless XDR looks like for organizations worldwide.