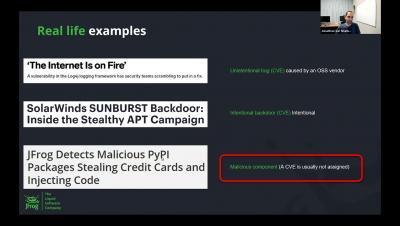
Create a Record
In this video, I will walk you through the creation of your first record. To begin, click the yellow Create New button and choose Record. You will notice a dropdown menu allows you to select the type of record you are creating. This allows users to create records of various template types, grouped into categories, each containing a unique collection of field types and functionality within the record. Examples of record types include: logins, payment cards, bank accounts, health insurance and many more. For more information on the Record Types feature, please see the video i’ve linked in the description below.