Rubrik and GraphQL - Episode 3 - GraphQL Mutations
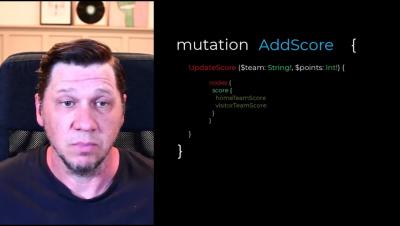
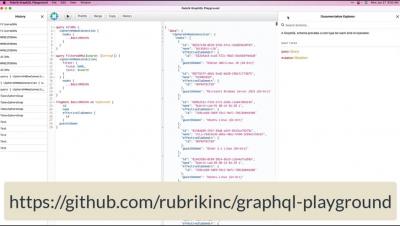
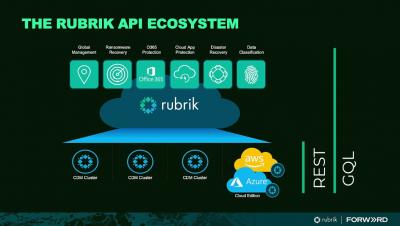
Mutations within GraphQL are simply queries that modify or change data within the target platform. In this episode, we will cover some of the various mutations available within the Rubrik GraphQL schema, and show you how they can be used to insert, update, or delete data.