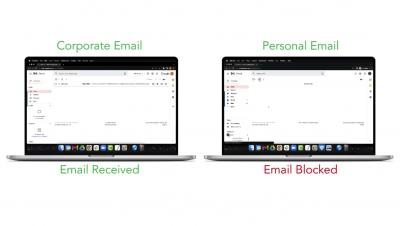
BlackHat 2022 key takeaways - Everything you need to know from BlackHat 25
Slides - BlackHat 25 was big, with hundreds of briefings, training sessions, vendor booths, and of course, parties, it is hard to get to everything. That's why this year we are covering the key trends and takeaways from the briefings of the 25th installment of BlackHat. This video covers 4 main takeaways This video covers a lot of different talks but if you want more information see links below to interesting blogs and whitepapers.