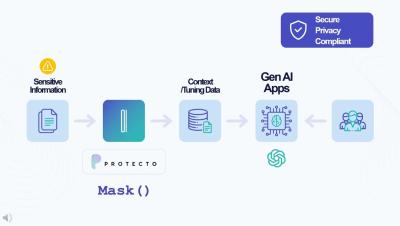
What is DAST (Dynamic Application Security Testing) 60 sec explainer
Discover the Power of DAST in Cybersecurity | Dynamic Application Security Testing Explained In the digital age, cyber threats are a constant concern. Protecting your organization's data and systems is paramount, and that's where DAST (Dynamic Application Security Testing) comes into play!