Product Quality at Rubrik - Part 2
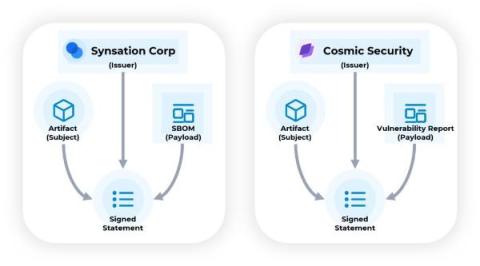
In our previous blog, we discussed the importance of product quality, different types of testing we rely on at Rubrik, and how automated testing plays a pivotal role in ensuring quality of our products. Relying heavily on Unit, Component and Integration testing is important. But there will be code paths which we may not be able to cover using these types of tests. In the picture below, we can see a high-level view of our solution.