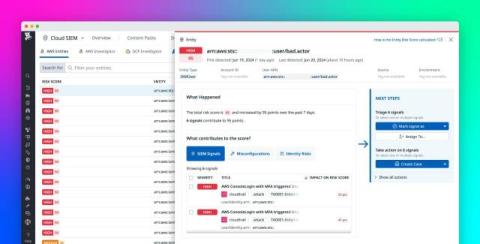
Accelerate investigations with Datadog Cloud SIEM Risk-based Insights and AWS Entity Analytics
Cloud environments today continue to grow in size and complexity, which increases the demand for improved security coverage in order to protect an organization’s assets, data, and reputation. This growth has also created significant and complex challenges in identifying insider or external threats, compromised accounts, and anomalous behavior across environments.