Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
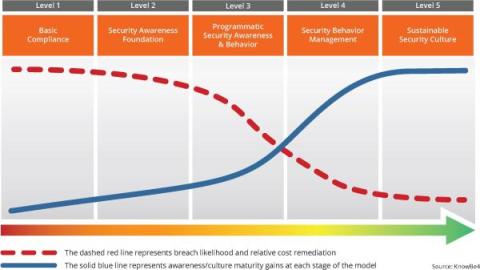
Phishing Tests Start The Virtuous Cycle Of A Strong Security Culture
Phishing tests are the catalyst to achieve a sustainable security culture within your organization. They are actually the start of a virtuous cycle that helps you move up to the highest maturity level. The cycle initiates with Awareness. Phishing tests offer a real-time view into your employees' understanding of phishing threats. They expose your workforce to simulated phishing attempts, making the threat real to them. The immediate feedback from these tests highlights areas for improvement.
Summit Sabotage: Malicious Phishing Campaign Hits Female Political Leaders Using Social Engineering
A threat actor dubbed “Void Rabisu” used social engineering to target attendees of the Women Political Leaders (WPL) Summit that was held in Brussels from June 7 to 8, 2023, Trend Micro has found. “Since many current and future political leaders had attended this conference, it presented an interesting target for espionage campaigns and served as a possible avenue for threat actors to gain an initial foothold in political organizations,” Trend Micro says.
Cyber Insurers Notes Ransomware Claims Rose Significantly in the First Half of 2023
Cyber insurers are claiming that cybercriminals made ransomware attacks popular again in 2023 after a slight break in 2022. According to cyber insurer Coalition's 2023 Cyber Claims Report, claims frequency increased by 27% in the first half of this year compared to the second half of 2022. Additionally, cyber insurer Resilience Cyber Insurance Solutions mid-year report showed a similar trend with 16.2% of its total claims were related to ransomware attacks.
What is a CMDB?
There are countless tools and technologies available to help an organization stay on top of its IT assets, and a configuration management database (CMDB) is an extremely useful one. The database keeps track of relevant information regarding various hardware and software components and the relationships between them. It allows IT teams to have an organized view of configuration items (CIs) that can enable more streamlined processes when it comes to IT work.
Save the Embarrassment: The Value of Multi-Factor Authentication
These days, it’s not a matter of if your password will be breached but when. Major websites experience massive data breaches at an alarming rate. Have I Been Pwned currently has records from 705 sites comprising 12.6 billion accounts. This includes well-known names like Wattpad, Verifications.io, and Facebook.
Voice of the SOC 2023
Security teams are getting restless. Before founding Tines, I spent 15 years in the SOC leading teams charged with protecting organizations from ever-evolving threats. Over that time, the challenge facing SOC analysts became harder, not easier: workloads are increasing, but teams aren’t growing alongside them. SOC analysts are burning out as a result of tedious and repetitive tasks.
Passkey vs Password: What's the Difference?
There are several ways in which passkeys are different from passwords in terms of how they are created, how they are filled into websites and how they are secured. Passwords are user-generated whereas passkeys are automatically generated using public key cryptography. Unlike passwords, passkeys are a new type of digital credential that is phishing-resistant and can’t be easily compromised. However, only a few websites currently support passkeys.
Secure Password and File Sharing for Federal and State Courts
U.S. court employees need to access dozens of systems and applications in order to complete their duties. These employees may also have access to Personally Identifiable Information (PII), which must be securely stored and managed with strict access controls. Court systems need a way for employees to easily and securely access systems, and share passwords and files among teams.
Get Management Buy-in with AppSec Metrics
Getting management to back your application security plans can be a tough sell. Metrics are vital because they help you understand how effective your initial cybersecurity measures are and how to turn them into measurable data that's easy for everyone to understand. This article will explore how to use metrics to get the support you need and make your application security programs more effective.