Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Privacy and Security on Windows: VPN Features Unveiled
Insider Risk Management for Your Cloud Infrastructure: Why Do You Need an IRM Program?
Detecting account compromise with UEBA detection packages
Weather Forecast: Money Is Going to Rain from the Cloud
Since the start of Bitcoin in 2009, the popularity and prevalence of cryptocurrencies has exploded, resulting in a net worth of over $1 trillion that continues to grow. Cryptocurrency—held in virtual wallets—is obtained by users who purchase coins on a cryptocurrency exchange, receive coins as payment from someone else, or “mine” coins virtually themselves.
DDoS attacks have increased by 40% over the last six months
Distributed denial-of-service (DDoS) attacks have been around for a long time. However, the sophistication and scale of these threats has grown in recent years. Cybercriminals are employing amplification techniques that exploit vulnerabilities in misconfigured services or network protocols to increase the traffic they can generate and maximize the impact of their attacks.
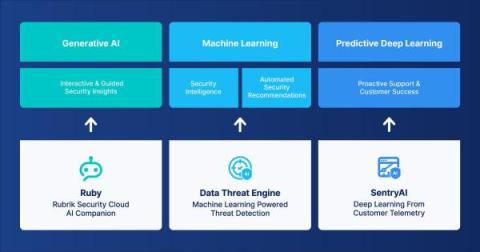
Announcing Ruby - your new Generative AI companion for Data Security
Say hello to Ruby, your new Generative AI companion for the Rubrik Security Cloud. Ruby is designed to simplify and automate cyber detection and recovery, something that IT and Security teams struggle with as cyber incidents are getting wildly frequent and the attacks are evolving quickly. A study by Rubrik Zero Labs revealed that 99% of IT and Security leaders were made aware of at least one incident, on average of once per week, in 2022.
Strengthening Cyber Defenses with Multi-Factor Authentication
The need for robust cyber defenses has never been more prevalent. We live in a world where remote access to data is the norm, opening up additional vulnerabilities when protecting digital assets. Additionally, organizations need to comply with data privacy requirements including understanding Digital Personal Data Protection. Mutli-Factor Authentication (MFA) isn’t a new concept. However, despite this, there is still confusion surrounding the mechanism and how it adds to cyber defense.
Introducing Vanta Trust Center and the State of Trust Report
Today we’re thrilled to introduce Vanta Trust Center, a centralized source of truth for companies to showcase their security posture confidently. Following Vanta’s acquisition of Trustpage earlier this year, Trust Center combines the capabilities of Trustpage Trust Centers and Vanta Trust Reports, making it easier than ever for customers to automatically manage their workflows and accelerate the security review process — all from within Vanta.
Calico Egress Gateway integration with AWS Network Firewall
Many AWS customers have security requirements that are well beyond what AWS Security Groups or AWS Network Access Control Lists can offer in terms of scalability and security. That’s why many of them turn to AWS Network Firewall as a common solution.