Introducing Dynamic Analysis MFA: Automated Support for MFA Setups
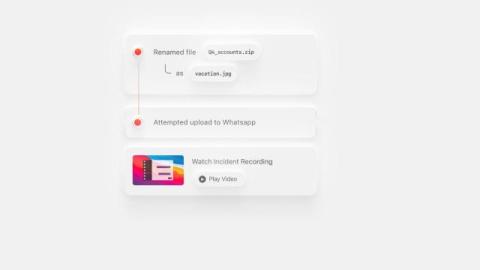
Veracode has recently introduced a new feature called Dynamic Analysis MFA, which provides automated support for multi-factor authentication (MFA) setups during dynamic analysis scans. This eliminates the need for you to disable or manually support your MFA configurations when conducting security testing.