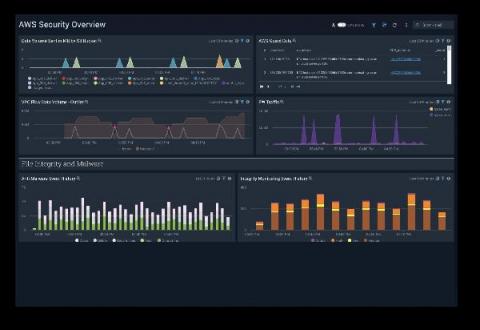
What Is Security Information and Event Management (SIEM)?
A cyberattack is expected to occur every 11 seconds in 2021 — nearly double the frequency just a year earlier. These incidents often involve breaches of sensitive proprietary information and cost the organizations involved millions of dollars. Despite all the resources being devoted to improving cybersecurity, new threats continue to arise faster than defense capabilities.