Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Is SIEM Suitable For My Organization?
Many people, when reviewing their security strategy, ask the question “is SIEM suitable for my organization”, or simply “is SIEM right for me?” And for a long time, the answer was “no unless you are a large multinational”. The price, the complexity and the hard-to-get value made SIEM a category suitable only for the big corporations with large security teams and budgets.
LogSentinel Honeypot: Malicious Actors Don't Wait
There’s an unwritten rule that every machine that becomes visible on the internet is under attack in under 5 seconds. We recently deployed our LogSentinel SIEM honeypot with one of our customers and that rule proved correct – immediately malicious requests from all over the world started pouring in, on almost all the protocols that we support – SSH, RDP, SMB, HTTP, and they haven’t stopped since.
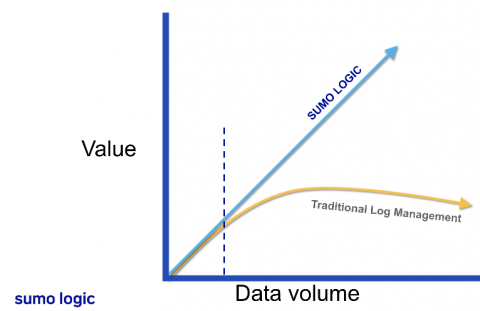
Building your modern cloud SIEM
The Three Pillars of SIEM
We have built our LogSentinel SIEM around some core principles and we’d like to share and explain them.
PSD2 Requirements and Secure Logs
PSD2 is the new EU Directive that aims to open up the banks and allow non-banking institutions to provide payment services. It is a great thing but it comes with many requirements. They are in the form of implementing and delegated acts of the European Commission as well as guidelines of the European Banking Authority. The directive, the implementing acts, and the guidelines are mostly best industry practices with regard to security and risk management.
SIEM Solutions and Data Protection Compliance
Security Information and Event Management (SIEM) systems are vital to each organization. They transform simple event logs from various applications to detailed, in-depth behavior analysis thanks to advanced visualizations and analytics and sometimes machine learning and AI. They contain a palette of aspects covering the most crucial information security issues.
Devo Next-Gen SIEM Honored by CISO Organization
Everyone at Devo is proud of the way our cloud-native logging and security analytics platform empowers security and operations teams to maximize the value of all their data. We have recently received kudos from industry analysts and awards from several industry organizations.
SIEM Tutorial: What should a good SIEM Provider do for you?
Modern day Security Information and Event Management (SIEM) tooling enterprise security technology combine systems together for a comprehensive view of IT security. This can be tricky, so we’ve put together a simple SIEM tutorial to help you understand what a great SIEM provider will do for you. A SIEM’s responsibility is to collect, store, analyze, investigate and report on log and other data for incident response, forensics and regulatory compliance purposes.
Why Are SIEMs Expensive?
SIEM (Security Information and Event Management) systems have a reputation for being expensive. And that’s generally correct – they can cost hundreds of thousands per year or have huge upfront costs. But why is that? There are several main reasons: All of this is changing. According to Gartner, SIEMs are going to the mid-market and these things don’t hold true there.