Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
New 1Password SIEM integration with Datadog
We’re thrilled to share that we’ve partnered with Datadog to give you greater visibility into the security posture of your business, all from one central location!
The SEC's new cybersecurity disclosure rules - are you ready?
Identifying malicious Remote Desktop Protocol (RDP) connections with Elastic Security
Is Your Supply Chain Partner Your Biggest Security Blind Spot?
Supply chain security issues are not exactly new. High-profile attacks, like SolarWinds in 2020, were a big wake-up call for many people because they brought home just how far-reaching and destructive these attacks could be. The threat from supply chain partners remains one of the most significant risks to security beaches. The SANS 2023 Attack and Threat Report found that 40% of breaches in 2022 occurred through supply chain partners.
Monitor 1Password with Datadog Cloud SIEM
1Password is a password manager that helps organizations reduce the use of weak and reused credentials across their teams. Because your organization uses 1Password to store highly sensitive information, including passwords, access keys, and secret tokens, monitoring logs generated by activity in your 1Password environment can be useful, as unexpected patterns of behavior could indicate malicious activity by attackers.
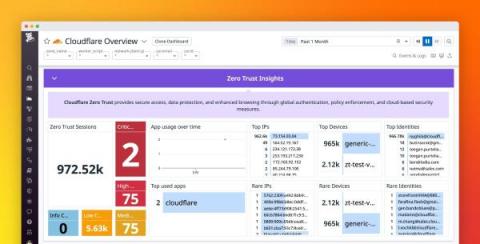
Monitor Cloudflare Zero Trust with Datadog Cloud SIEM
Cloudflare’s SASE is a zero trust network-as-a-service platform that dynamically connects users to enterprise resources, with identity-based security controls delivered close to users, wherever they are. Cloudflare spans more than 300 cities in over 100 countries, resulting in latencies under 50 milliseconds for 95 percent of the internet-connected population globally.