Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
How to Use Google SIEM: A Complete Guide
What do you know about how to use Google SIEM? You can read about implementing these managed security services into your company's network protocols.
Elastic and other security leaders working to make OTel Semantic Conventions a standard across Observability and Security data
Security analyst FAQ: everything you need to know for a career in cybersecurity
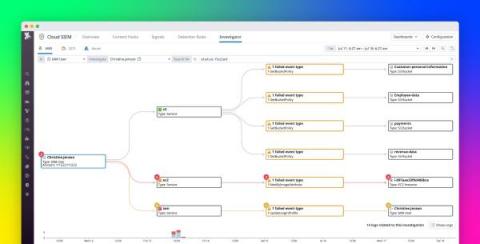
Conduct historical security investigations with Datadog Cloud SIEM Investigator
As organizations increase the size of their cloud footprint and the complexity of their applications, they face challenges securing their infrastructure and services. Security breaches often go undetected for months, giving attackers time to do extensive harm. Once organizations become aware of a breach, they may no longer have access to the logs that comprise a complete history of the attack, because the time span easily exceeds their log retention window.
Automating insight into SEC cybersecurity filings with Elastic
Integrate Cloudflare Zero Trust with Datadog Cloud SIEM
Cloudflare's Zero Trust platform helps organizations map and adopt a strong security posture. This ranges from Zero Trust Network Access, a Secure Web Gateway to help filter traffic, to Cloud Access Security Broker and Data Loss Prevention to protect data in transit and in the cloud. Customers use Cloudflare to verify, isolate, and inspect all devices managed by IT. Our composable, in-line solutions offer a simplified approach to security and a comprehensive set of logs.
Server Security: What it is and How to Implement It
ManageEngine Recognized as a Customers' Choice in 2023 Gartner Peer Insights 'Voice of the Customer': Security Information and Event Management (SIEM) for the fourth time
We’re thrilled to announce that ManageEngine has once again been recognized as a Customers’ Choice in the 2023 Gartner Peer Insights ‘Voice of the Customer’: Security Information and Event Management (SIEM). This marks the fourth time that ManageEngine has been recognized as a Customers’ Choice, which we believe is a testament to our commitment to providing our customers with exceptional SIEM solutions.