Fueling the SOC of the Future with Built-in Threat Research and Detections in Splunk Enterprise Security
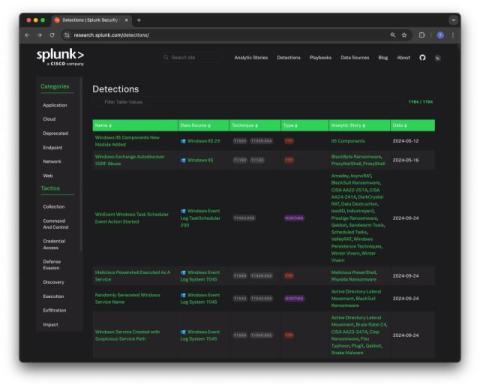
The cybersecurity threat landscape is ever-changing and evolving, with bad actors implementing increasingly sophisticated strategies to evade detection. However, many security teams struggle to adapt their detection strategies at the same pace. Supporting advanced threat detection requires organizations to invest in consistent threat research and detection engineering. Without that, they cannot develop the high-quality detections needed to target the latest threats.