Using Devo to Stop Black Kingdom ProxyLogon Exploit
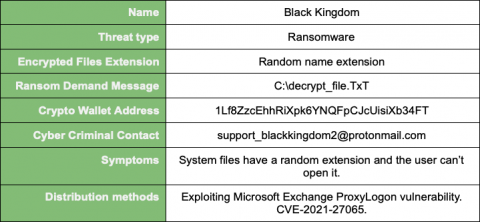
Black Kingdom is targeting Exchange servers that remain unpatched against the ProxyLogon vulnerabilities disclosed by Microsoft earlier this month. It strikes the on-premises versions of Microsoft Exchange Server, abusing the remote code execution (RCE) vulnerability also known as ProxyLogon (CVE-2021-27065[2]).