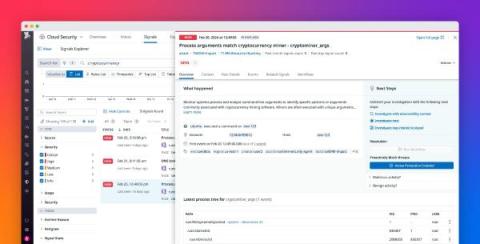
Report on changes to your security posture with Cloud Security Management
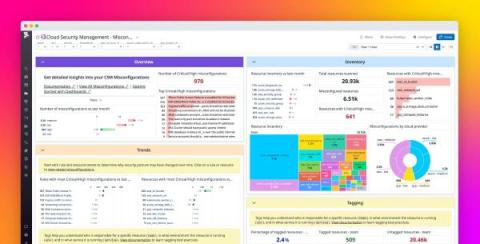
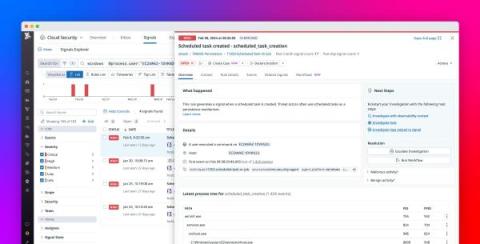
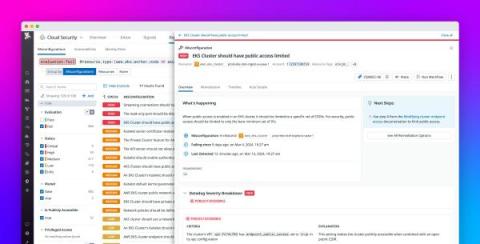
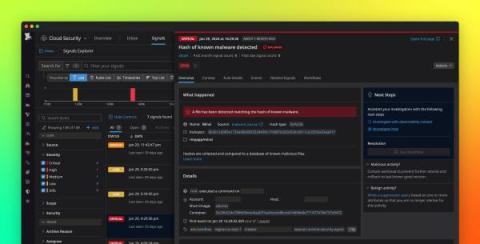
Achieving and maintaining compliance in the cloud proves challenging for many organizations, as it is a complex, ongoing effort that includes safeguarding sensitive data and ensuring infrastructure resources are correctly configured. Success often hinges on the ability to monitor compliance-related trends over time, enabling organizations to spot risk patterns, gauge their current compliance posture, and adapt as new risks emerge. However, gathering this data can be difficult.