How financial services companies discover, classify, and manage sensitive data with Datadog
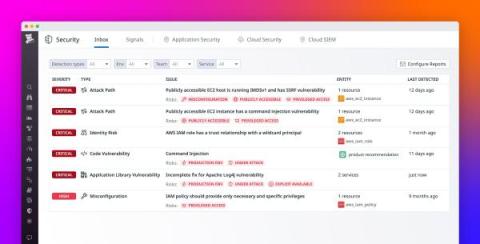
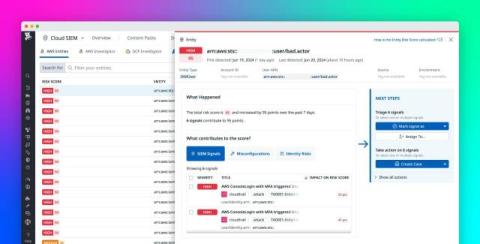
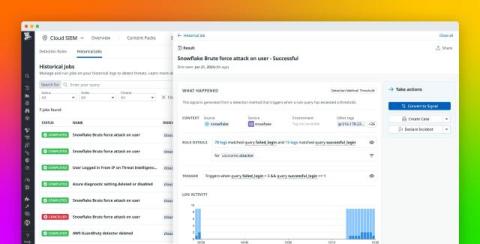
As financial services companies, such as banks, hedge funds, and stock exchanges, move to the cloud, sensitive data often unintentionally moves with them. To help avoid costly breaches and address governance, risk, and compliance (GRC) requirements such as PCI-DSS, GDPR, and SOC 2, these organizations may need to identify where in the cloud sensitive data can leak and be able to redact it at scale.