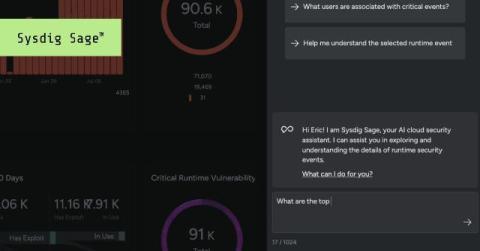
Sysdig Sage for CDR: Accelerate analysis, investigation and response
Last year, Sysdig outlined our vision for an AI-driven cloud security assistant. Today, we are excited to announce Sysdig Sage for cloud detection and response (CDR), our new release that embodies our vision. Built upon the core principles we introduced, Sysdig Sage offers actionable insights for cloud environments, with a focus on CDR.