Detectify honored as Market Leader in Attack Surface Management in Global InfoSec Awards
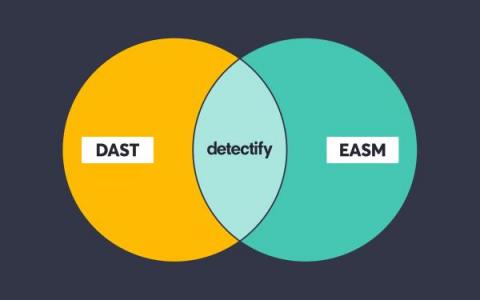
Detectify is honored to start off the RSA 2023 Conference with the news that it has been recognized as the market leader in Attack Surface Management in Cyber Defense Magazine’s Global InfoSec Awards. This accolade demonstrates the effectiveness of Detectify’s approach to External Attack Surface Management (EASM), which is unique in the space because it tests environments with real payloads by using its crowdsourced community of ethical hackers.