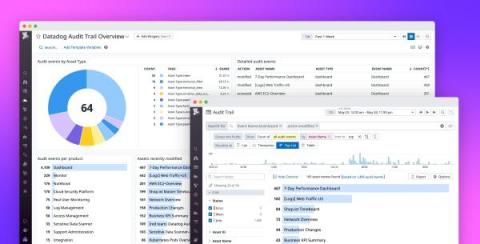
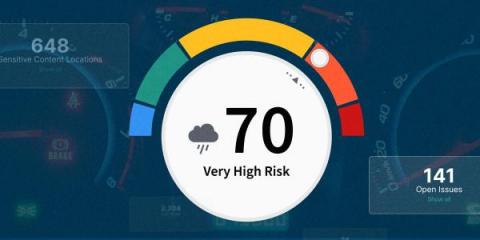
Ensure compliance, governance, and transparency across your teams with Datadog Audit Trail
In order to maintain compliance, enforce governance, and build transparency, teams across your organization need deep insight into how their users and automation interact with Datadog. For stakeholders in leadership roles, such as CIOs and CDOs, knowing what actions users took and when is essential for spotting gaps in enablement, budgeting, and reporting, as well as building a modern compliance strategy for the organization as a whole.