Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
What is Styra Declarative Authorization Service?
Whether you’re a developer or an IT professional (or a bit of both!), enforcing and managing authorization policies for the new containerized world is a whole different ball game than it was before. There’s the complex nature of modern applications — composed of multiple microservices, housed in containers — and then there’s the dynamic nature of platforms like Kubernetes, running those applications.
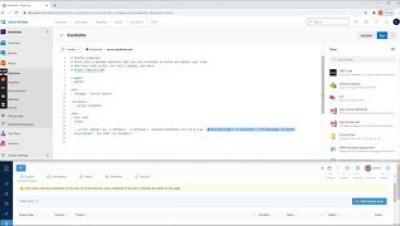
How to Run Security Checks in CI/CD with Kondukto?
Unify Access to Cloud - Iterating on Identity-Based Management
The maturation of software development has been driven by the increasing segmentation of functions into their own portable environments. Infrastructure is splintered into dozens of computing resources, physical servers, containers, databases, Kubernetes pods, dashboards, etc. Such compartmentalization has made it incredibly simple for developers to enter their desired environments with minimal disruption to other working parts.
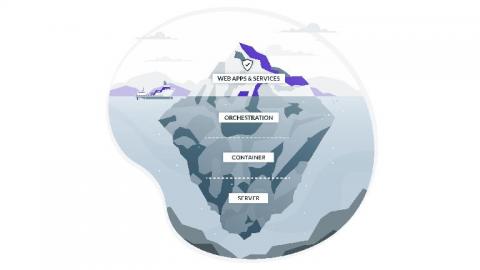
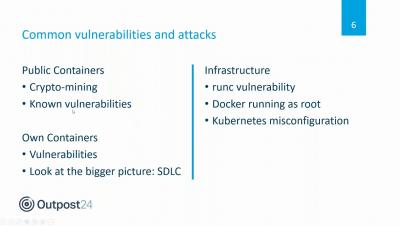
Outpost24 Webinar: Mastering container security in modern day DevOps
Automate vulnerability analysis with the Datadog GitHub Action
To enhance and automate your vulnerability analysis, we’re excited to launch the Datadog Vulnerability Analysis GitHub Action. The action enables easy integration between your application, Datadog Continuous Profiler, and Snyk’s vulnerability database to provide actionable security heuristics. The action can be installed directly from the GitHub Marketplace, and does not require you to manage any additional scripts or infrastructure.
2021 Predictions: The Year that Cloud-Native Transforms the IT Core
Continued Kubernetes adoption, unified authorization, DevSecOps redefined, open source dominance and more key changes for the enterprise Amid a year of unprecedented global change, it may seem incautious at best to make confident predictions about the future of cloud-native business. However, there are strong indications of the trends that 2021 will hold — precisely because they are predicated on significant enterprise change.
Adding Helm Chart Security Mitigation Notes to ChartCenter
Earlier this year, we launched ChartCenter, our newest community platform to help Kubernetes developers find Helm charts. This new free Helm central repository was built with chart immutability in mind— meaning every version of a Helm chart and every version in ChartCenter will always be available even if the original source goes down.
ARMO Announces Nitro Enclave support - making it DevOps ready out of the box
Enabling enclaves-based security is key for enterprise cloud adoption General availability of Nitro Enclaves, recently announced by AWS, is Amazon’s way of delivering confidential computing to its customers. Following similar announcements by Microsoft Azure and Google Cloud, AWS announcement further confirms growing demand for additional runtime protection of customer’s data and other intellectual properties.
The Pitfalls of Language Runtimes and Multi-tenant Services
Modern languages like Python, NodeJS, and Go make it easy to handle concurrent requests for multiple customers at the same time by using threads or goroutines. Such services seem very cost effective because one process can handle hundreds or thousands of tenants. However, this efficiency comes at a hidden, steep price. When language runtime scheduling breaks down, one tenant can cause an outage for everyone.