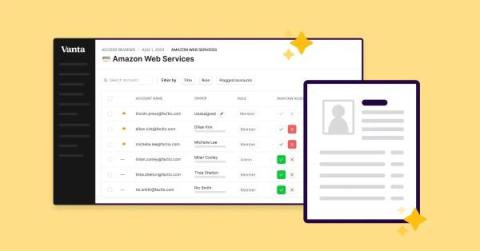
Introducing AI Data Import for Access Reviews
Conducting regular user access reviews is an effective way to make sure your organization is securing access to critical systems and third-party vendors. Frameworks like SOC 2 and ISO 27001 even require proof of regular access reviews to demonstrate compliance. Without automation, access reviews are tedious and time-consuming, requiring IT and security teams to manually record user access information in a spreadsheet and take countless screenshots of access permissions screens.