Streamlining Legal Workflows with NotatePDF
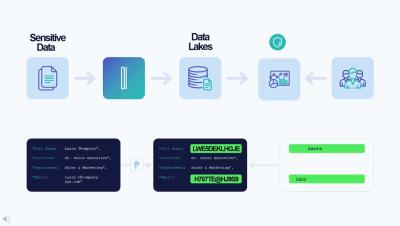
In the fast-paced world of legal practice, managing cases, documents, and communication is a constant challenge. Legal professionals must juggle numerous tasks, from drafting and reviewing documents to coordinating with clients and colleagues. The sheer volume of information and the need for accuracy and timeliness often lead to inefficiencies, errors, and missed deadlines. These challenges are further compounded by the demand for secure handling of sensitive data and compliance with strict regulations.