Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Cloud
Cloudflare Cache Reserve Walkthrough and Demo
The Shift to the Cloud and its Implications for Application Security
Everybody’s doing it: shifting applications to the cloud. More flexibility. More storage. More scalability. But how does this affect application security? What challenges does it present?
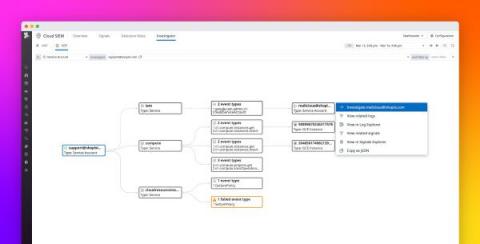
Visualize activity in your Google Cloud environment with Datadog Cloud SIEM Investigator
Cloud environments, in all their dynamic complexity, demand careful monitoring by DevOps and security teams. But the sheer abundance of telemetry data associated with the thousands of resources, users, and roles that comprise these environments can make monitoring a formidable task, causing security risks and other issues to be all too easily overlooked.
Netskope Modern DLP
How to Handle AWS Secrets
In this blog post, we'll cover some best practices for managing AWS secrets when using the AWS SDK in Python.
Top 6 Cloud Insider Threats You Need To Be Aware Of
Cloud computing is the most cost-effective way to store and manage data and meet growing business demands today. However, the rapid rise of cloud usage means you need to stay alert to potential cloud security insider threats that can compromise your sensitive data and security posture. In this post, we discuss the insider threat landscape, explore several types of cloud insider threats, and examine the best practices to combat these threats.
Everything you might have missed during Security Week 2023
Security Week 2023 is officially in the books. In our welcome post last Saturday, I talked about Cloudflare’s years-long evolution from protecting websites, to protecting applications, to protecting people. Our goal this week was to help our customers solve a broader range of problems, reduce external points of vulnerability, and make their jobs easier. We announced 34 new tools and integrations that will do just that.
Account Security Analytics and Events: better visibility over all domains
Cloudflare offers many security features like WAF, Bot management, DDoS, Zero Trust, and more! This suite of products are offered in the form of rules to give basic protection against common vulnerability attacks. These rules are usually configured and monitored per domain, which is very simple when we talk about one, two, maybe three domains (or what we call in Cloudflare’s terms, “zones”).