Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
AST
FuzzCon Europe - Automotive Edition 2022
SAST - All About Static Application Security Testing
Static Application Security Testing (SAST) has been a central part of application security efforts for more than 15 years. Forrester’s State Of Application Security Report, 2022 found that lacking application security remains a leading cause of external security breaches, so it’s safe to say that SAST will be in use for the foreseeable future. Contents hide 1 What Is SAST? 2 Why do we need SAST? 3 What problems does SAST address? 4 How does SAST work?
SAST - All About Static Application Security Testing
Static Application Security Testing (SAST) has been a central part of application security efforts for more than 15 years. Forrester’s State Of Application Security Report, 2022 found that lacking application security remains a leading cause of external security breaches, so it’s safe to say that SAST will be in use for the foreseeable future.
Embedded Testing Tools: A Comprehensive Guide
Due to increasing connectivity and dependencies, modern embedded applications in many industries including automotive, aviation, and even automated cow brushes (no joke) are constantly growing more complex. This complexity comes with implications for embedded testing tools and requires plenty of manual effort, depending on the toolchain. From an operational perspective, many embedded industries are tightly staffed and work in long cycles with strict deadlines.
How Can Fuzzing Help Find Bugs in Hardware?
The growing complexity of embedded systems coupled with the advent of increasingly sophisticated security attacks highlights a dire need for advanced automated vulnerability analysis tools. Fuzzing is an effective proven technique to find security-critical issues in systems, often without needing to fully understand the internals of the system under test.
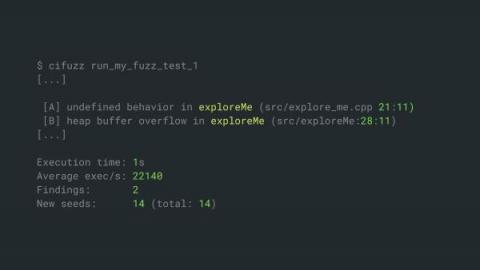
Secure Coding in C and C++ Using Fuzz Testing
Today, I would like to show you to a simplified fuzz testing approach that enables secure coding of C and C++ applications. If you read this article to the end, you will learn about an automated security testing approach for C/C++ that can protect your applications against all sorts of memory corruptions and other common C/C++ vulnerabilities.
Scalable SAST and SCA in a single solution with Polaris fAST services
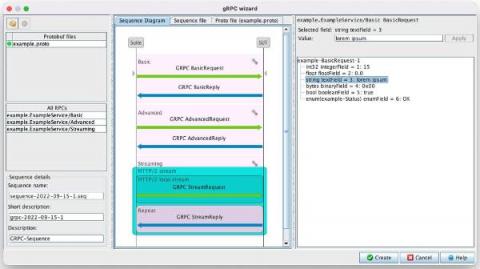
Defensics adds gRPC support for distributed web and mobile application security testing
Choosing a DAST solution: What to pay attention to?
The majority of today's web applications contain dangerous vulnerabilities. To analyze their security, one cannot do without a dynamic scanner. DAST (Dynamic Application Security Testing) tools allow you to detect and evaluate security problems quickly. Let me tell you what to look for when choosing such a tool.