Remote Code Execution Vulnerability Discovered in HSQLDB
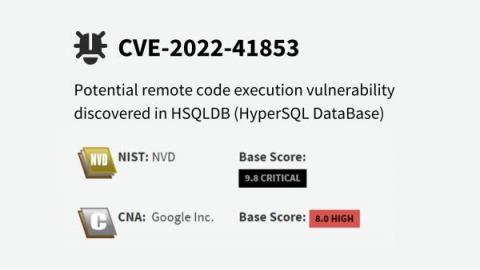
19.10.2022 - As part of our goal to continuously improve our vulnerability detectors, we continuously test various open-source projects with Jazzer within OSS-Fuzz. In this case, a test run yielded a severe finding with a potential remote code execution in a HSQLDB (CVE-2022-41853).