Using AWS Session Manager with Enhanced SSH and SCP Capability
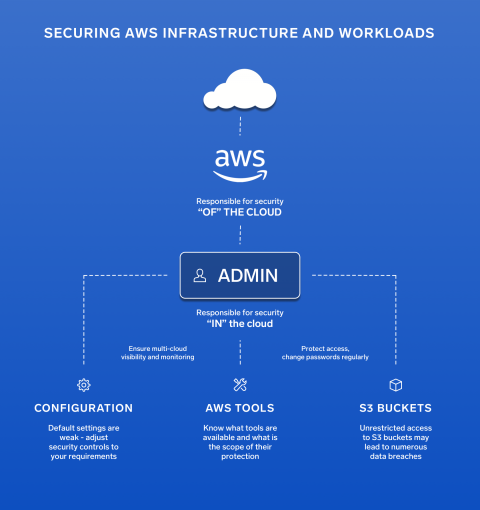
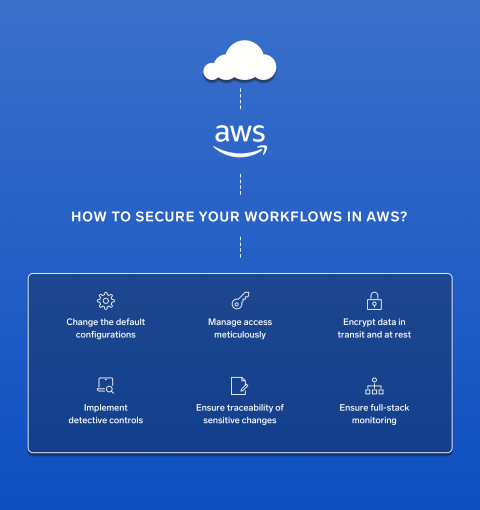
Amazon Web Services recently announced new capabilities in the AWS Systems Manager Session Manager. Users are now capable of tunneling SSH (Secure Shell) and SCP (Secure Copy) connections directly from a local client without the need for the AWS management console. For years, users have relied on firewalls and bastion hosts in order to securely access cloud assets, but these options have security and management overhead tradeoffs.