Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Technology
Predictions 2021: We Now Live in a Truly Mobile-first World
Over the past decade, technology enthusiasts have dreamed about smartphones and tablets taking over various aspects of our lives. They have in many ways, but the shift has always been gradual. This all changed in 2020 when most of us were forced to stay home. From the way we work, go to school, interact with our healthcare providers, manage our finances, shop, and connect with friends and families – mobile is now at the center of our lives.
Top 10 Open Source Vulnerabilities In 2020
If 2020 taught us anything, it’s to expect the unexpected. While there don’t seem to be enough words to cover the changes that we all did our best to adjust to, we are more than happy to give you our rundown of the top 10 open source vulnerabilities in 2020.
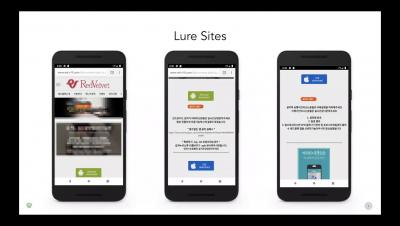
Lookout Discovers New Spyware Used by Sextortionists to Blackmail iOS and Android Users
The Lookout Threat Intelligence team has discovered a new mobile app threat targeting iOS and Android users in Chinese speaking countries, Korea and Japan. The spyware, which we have named Goontact, targets users of illicit sites, typically offering escort services, and steals personal information from their mobile device. The types of sites used to distribute these malicious apps and the information exfiltrated suggests that the ultimate goal is extortion or blackmail.
Introducing Teleport Cloud | Access Management SaaS | Servers - Clusters - Applications
Secure Your Cloud Transformation with Continuous Intelligence
Netskope Threat Coverage: SUNBURST & FireEye Red Team (Offensive Security) Tools
On Dec 8, 2020, the cybersecurity company FireEye reported that there had been a cyber attack on their systems. As part of this attack, their inventory of Red Team tools was stolen. These tools could potentially be used by a threat actor against unsuspecting victims. On Dec 13, 2020, after further investigation of this attack, FireEye reported that the initial vector came through SolarWinds, an upstream vendor, as a malicious trojanized update of SolarWinds’ Orion IT platform.
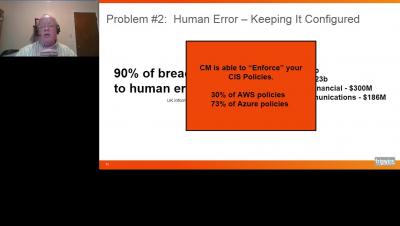
Secure Your Journey to the Cloud with Tripwire Configuration Manager
What New Zealand's Privacy Act 2020 means for APIs
On December 1st 2020, New Zealand’s revamped privacy act went into effect. The Privacy Act originally passed in 1993 and has been revisited multiple times, but the 2020 act clarifies its reach and outlines what organizations need to do in order to be compliant.
Cloud Security: Messy Blobs and Leaky Buckets
Moving to the cloud means a lot more than just moving your servers and applications to the cloud; it’s also about the data – and data always has a target on it. A lot of IT departments are finding that it’s easier to meet the “five nines” (99.999%) of uptime and availability by going outside their organization and letting AWS, Microsoft, or Google handle the infrastructure and personnel needed to meet those requirements.