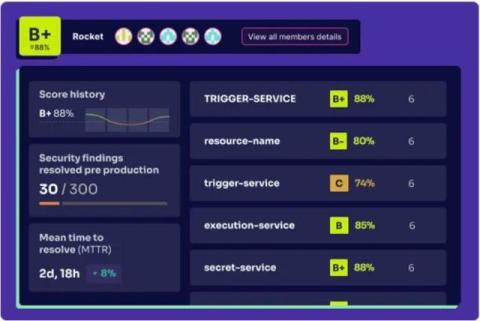
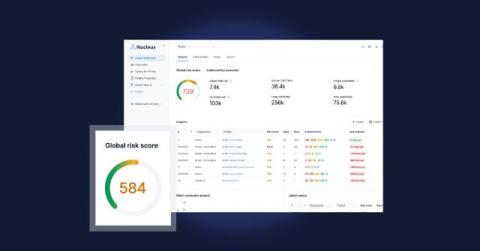
Empower Development Teams to Own the Security of Their Services with Jit Teams
When it comes to securing applications in the cloud, the challenge isn’t detecting potential security issues. There are hundreds of application security tools and cloud security tools that are capable of surfacing code flaws and security misconfigurations that could lead to vulnerabilities. The real challenge is empowering development teams to adopt these tools to consistently improve the security posture of their services.