Cloud Threats Memo: How Leaky Are Your Cloud Apps?
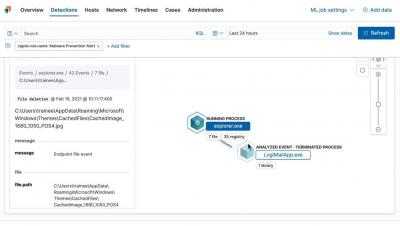
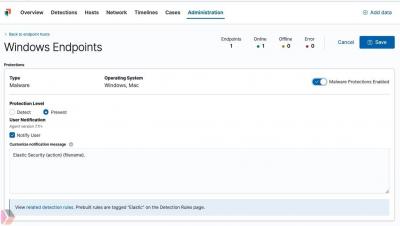
Leaky cloud services are a major concern these days. As more and more organizations move their data and applications to the cloud, ensuring new forms of collaboration and agility for their workforce, setup errors and misconfigurations (or even the lack of understanding of the shared responsibility model) pose a serious risk for the new, enlarged corporate perimeter. So far, in 2021, I have collected 12 major breaches fueled by cloud misconfigurations, and I wonder how many flew under the radar.