Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Popular JavaScript Library ua-parser-js Compromised via Account Takeover
A few hours ago, an npm package with more than 7 million weekly downloads was compromised. It appears an ATO (account takeover) occurred in which the author’s account was hijacked either due to a password leakage or a brute force attempt (GitHub discussion).
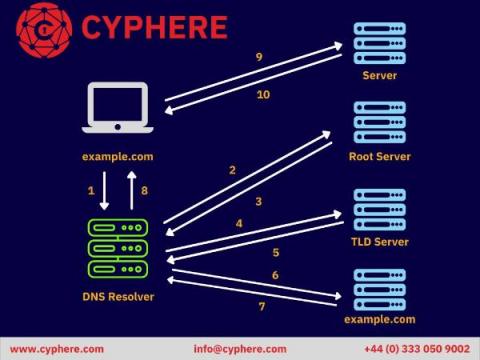
What is DNS hijacking? Redirection Attacks Explained (and Prevention)
Almost everybody in this world uses the Internet. Some use it for work, some for education, some to stay connected with the world and their loved ones, some for shopping, and some use it to browse the world wide web in their leisure time. DNS Hijacking or DNS redirection attacks are a widespread security threat many DNS servers face in today’s modern digital world.
What is Data Protection by Design?
‘Privacy by design’, or as it’s now known, ‘data protection by design and default’, refers to Article 25 of the UK GDPR. This principle makes it a legal obligation for controllers to implement organisational controls which ensure data protection issues are addressed at the design stage of any project. But what does the regulation mean when it refers to organisational controls?
What is Vendor Risk Management? Your go to VRM guide
Vendor risk management (VRM) is the type of risk management practice assessing and mitigating business partners, third parties, or external vendors. This process is conducted before an entity enters into a business relationship and during the duration of the business contract with the vendor.
Vendor Risk Management: Best Practices for 2021
Vendor risk management (VRM) is rapidly emerging with ever-evolving cyber security strategies. As we hit the pandemic and try to manage critical operations in a remote work setup, each day, business entities challenge with the new security, privacy, and business continuity risks associated with their vendors.
How can I secure my Android app's code?
Android is the world’s most widely used operating system. And we’re huge fans of it here at Conseal. But building Android apps can present some unique security challenges to developers. These may be for example as a result of the way that Android operates, the hardware that runs it, or its Linux heritage. This blog post outlines some of the things that our code auditors and penetration testers look for when reviewing Android apps for security vulnerabilities.
Weekly Cyber Security News 22/10/2021
A selection of this week’s more interesting vulnerability disclosures and cyber security news. For a daily selection see our twitter feed at #ionCube24. Quite an interesting bunch this week. You know when you cover the pad with your hand to hide your pin at ATM? Well that might not be enough soon – given time I’m sure they will get better at guessing.