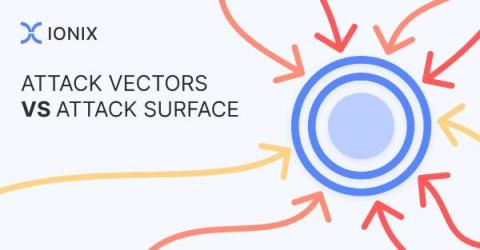
How are Attack Vectors Related to Your Attack Surface?
In the world of cybersecurity, two terms frequently dominate discussions among professionals: “Attack Surface” and “Attack Vectors”. At first glance, these concepts might appear separate, but they are intricately linked, shaping the way security experts strategize and implement defenses.