Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
IONIX
The rise of ChatGPT & GenAI and what it means for cybersecurity
Security Validation Explained: A Trusted Path to Risk Reduction
How to prevent credential stuffing in 3 steps (e.g. naz.API)
Asset Importance: The Overlooked Factor in Cyber Risk Prioritization
What is Cybersecurity Risk Management?
The Complete Vulnerability Assessment Checklist
Navigating the Shift: From Vulnerability Management to Continuous Threat Exposure Management
In the rapidly evolving cybersecurity landscape, organizations face an ever-increasing barrage of threats. Traditional vulnerability management, while foundational, often falls short in proactively and continuously identifying and mitigating threats. This necessitates a paradigm shift towards Continuous Threat Exposure Management (CTEM), a more dynamic approach that aligns with the complexities of today’s digital environments.
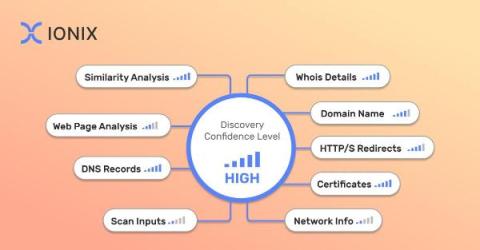
How to Implement Multi-Factor Asset Attribution in Attack Surface Discovery
As organizations navigate through the complexities of the digital era, the challenge of accurately identifying and managing their asset inventory has become a critical aspect of their security posture. This task, known as attack surface discovery and asset attribution, involves a delicate balance: identifying all assets that belong to the organization while ensuring that no extraneous ones are included.
How to Improve Security Hygiene and Posture Management with ASM
Security hygiene and posture management (SHPM) is a relatively new concept, yet it’s fundamental to protecting sensitive systems and data. There’s growing recognition that it’s critical for today’s companies to fully understand assets and their relationships. As a result, more companies are looking to SHPM as a core component of their cybersecurity programs.