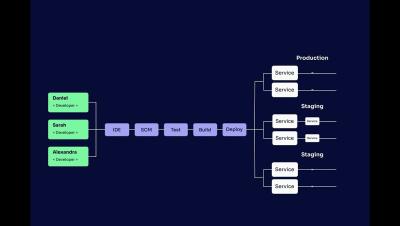
Securing Web Apps on a Lean Budget Amid Economic Uncertainty and Growing Data Breaches
The cyber threat landscape is continuously evolving and becoming more dangerous with the rise of application attacks and data breaches, putting businesses at greater risk. Verizon’s 2024 Data Breach Investigations Report saw a record-high number of breaches—more than 10,000, doubling the number of breaches it analyzed from 2023.