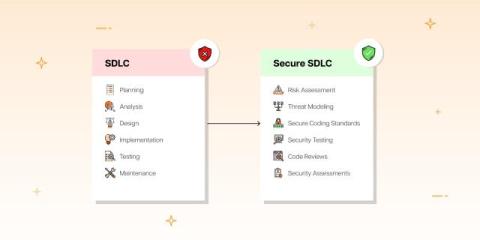
The AI Revolution: Balancing Innovation and Ethics in the Age of Intelligent Technology
Artificial intelligence (AI) is revolutionizing most, if not all, industries worldwide. AI systems use complex algorithms and large datasets to analyze information, make predictions and adjust to new scenarios through machine learning – enabling them to improve over time without being explicitly programmed for every task.