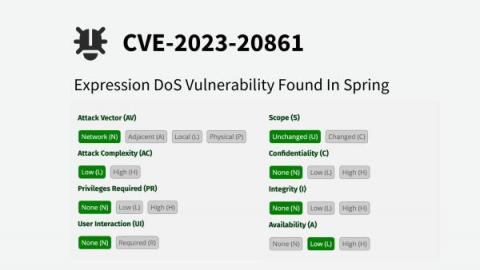
Expression DoS Vulnerability Found in Spring - CVE-2023-20861
As part of our efforts to improve the security of open-source software, we continuously test open-source projects with our JVM fuzzing engine Jazzer in Google’s OSS-Fuzz. One of our tests yielded a Denial of Service vulnerability in the Spring Framework (CVE-2023-20861). Spring is one of the most widely used frameworks for developing web applications in Java. As a result, vulnerabilities have an amplified impact on all applications that rely on the vulnerable version.