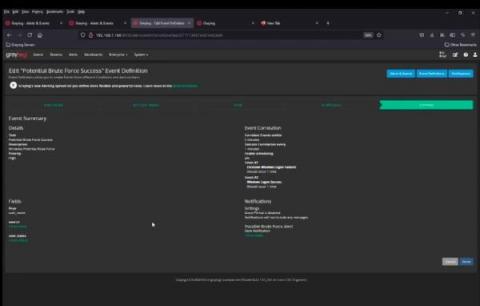
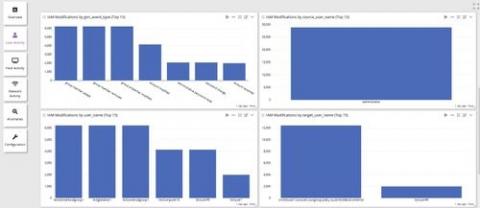
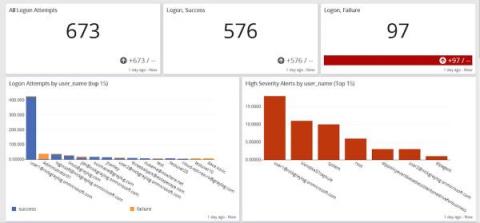
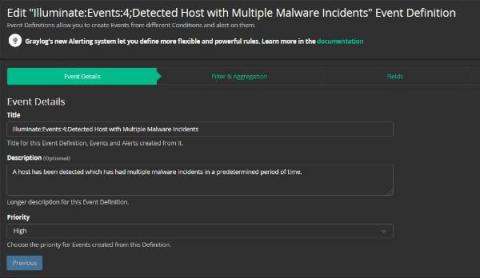
Graylog Security - The Affordable SIEM Alternative
Cyber resiliency is the new norm in cybersecurity. Nothing can be 100% secure, and you’re looking for a cost-effective solution to enhance your security posture. At the same time, the rapidly expanding cybersecurity technology market makes it hard to find something that best fits your needs. Most people looking at Security Information and Event Management (SIEM) platforms want a tool that gives them high fidelity alerts to prevent their security analysts from drowning in false positives.