The Software Supply Chain Risks You Need to Know
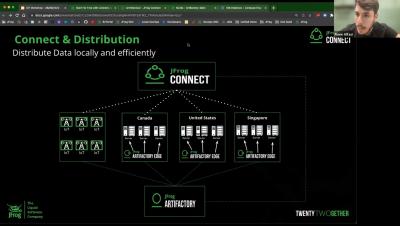
Code that an organization’s developers create is only the beginning of modern software development. In fact, first-party code is likely to be only a small proportion of an application – sometimes as little as 10% of the application’s artifact ecosystem. An enterprise’s software supply chain is made of many parts, from many sources: open source packages, commercial software, infrastructure-as-code (IaC) files, and more.