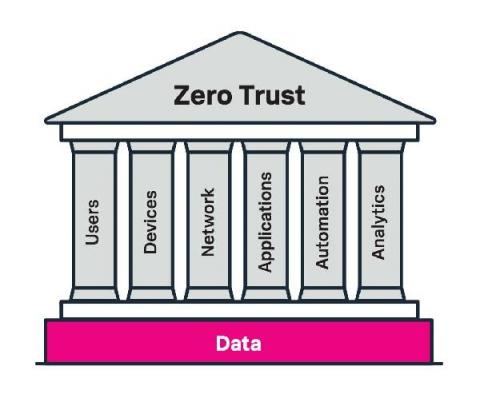
Fashionably Late: The Zero Trust Trend is Here to Stay
I have often joked that IT, and in particular cybersecurity, is like fashion — not a lot is ever new, just reimagined and, in some cases, improved. As I sit pondering the beauty of my COVID-19 comb-over mullet, I have found myself thinking about how this fashion analogy applies to zero trust.