Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Tigera
Egress access control for Kubernetes
Now GA: Data-in-Transit Encryption in Calico v3.15
We’re excited to announce that the latest release of Calico includes encryption for data-in-transit. Calico is the open source networking and network security solution for containers, virtual machines, and host-based workloads, offering connectivity and security for container workloads. One of Calico’s best-known security features is its implementation of Kubernetes Network Policy, providing a way to secure container workloads by restricting traffic to and from trusted sources.
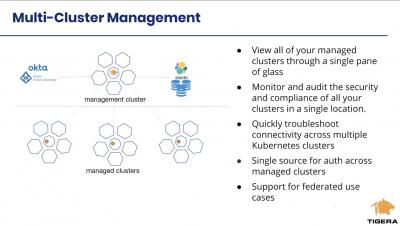
Introduction to multi cluster security using Calico Enterprise
On-Demand Webinar: Extending Your Fortigate Next-Gen Firewall to Kubernetes
Kubernetes Security: Lateral Movement Detection and Defense
What is Lateral Movement? Lateral movement refers to the techniques that a cyber-attacker uses, after gaining initial access, to move deeper into a network in search of sensitive data and other high-value assets. Lateral movement techniques are widely used in sophisticated cyber-attacks such as advanced persistent threats (APTs).
Calico Egress Gateway: Universal Firewall Integration for Kubernetes
New applications and workloads are constantly being added to Kubernetes clusters. Those same apps need to securely communicate with resources outside the cluster behind a firewall or other control point. Firewalls require a consistent IP, but routable IPs are a limited resource that can be quickly depleted if applied to every service.