Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Veracode
Just Because You Don't Use Log4j or Spring Beans Doesn't Mean Your Application is Unaffected
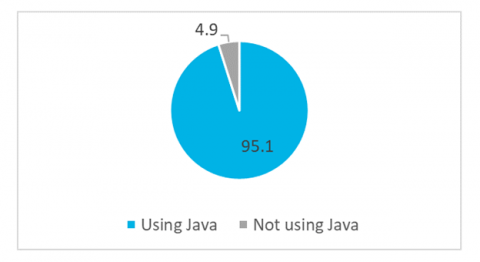
By now, you’re probably all aware of the recent Log4j and Spring Framework vulnerabilities. As a recap, the Log4j vulnerability – made public on December 10, 2021 – was the result of an exploitable logging feature that, if successfully exploited, could allow attackers to perform an RCE (Remote Code Execution) and compromise the affected server.
Veracode Acquires ML-Powered Vulnerability Remediation Technology From Jaroona GmbH
On the heels of our significant growth investment from TA Associates, we are pleased to announce our acquisition of auto-remediation technology from Jaroona. Jaroona’s intelligent remediation technology accelerates Veracode’s vision and strategy to automatically detect and remediate software vulnerabilities. Jaroona was recognized as a Gartner Inc. 2021 Cool Vendor for DevSecOps.
Testing OWASP's Top 10 API Security Vulnerabilities (Part 1)
Application Programming Interface (API) attacks are set to become one of the most prevalent cyberattacks with a broad target range. By nature, APIs expose application logic and sensitive data such as personally identifiable information (PII), causing APIs to become a target for attackers. In 2019, Gartner predicted that API hacks would become the most common form of cyberattacks in 2022. So how can teams stay ahead of API attacks?
Spring4Shell Vulnerability vs Log4Shell Vulnerability
On March 29, 2022, details of a zero-day vulnerability in Spring Framework (CVE-2022-22965) were leaked. For many, this is reminiscent of the zero-day vulnerability in Log4j (CVE-2021-44228) back in December 2021.
Spring Framework Remote Code Execution (CVE-2022-22965)
Details of a zero-day vulnerability in Spring Framework were leaked on March 29, 2022 but promptly taken down by the original source. Although much of the initial speculation about the nature of the vulnerability was incorrect, we now know that the vulnerability has the potential to be quite serious depending on your organization’s use of Spring Framework. There is also a dedicated CVE 2022-22965 assigned to this vulnerability. We will keep this blog updated as new information comes up.
Veracode Product Update
The Public Sector Has the Highest Proportion of Security Flaws of Any Industry
We recently launched the 12th annual edition of our State of Software Security (SOSS) report. To draw conclusions for the report, we examined the entire history of active applications. For the public sector data, we took the same approach. We examined the entire history of applications for government agencies and educational institutions. We found that the public sector has the highest proportion of security flaws of any industry.
Shifting Log4j Discovery Right
You hear a lot about shifting your application security (AppSec) left – in other words, shifting AppSec to the beginning of the software development lifecycle (SDLC). While we firmly believe that you should continue scanning in development environments, that doesn’t mean that you should neglect applications that have been deployed to or staged in runtime environments.