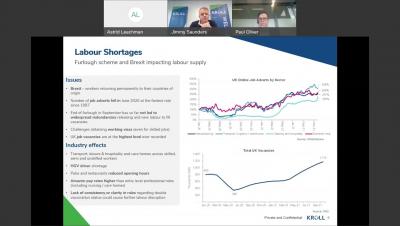
Locking Your Domain Name Helps Fight Cybercrime
Ransomware and cybercrime have had a major presence in the media this past year with some very prominent attacks happening in 2021 making headlines as well as government-issued executive orders emphasizing the need for stronger cybersecurity. This has resulted in many organizations taking action to bolster their security efforts which can make it difficult for cyber criminals to successfully conduct their attacks.