3 Reasons Log Management is Critical for Business Intelligence
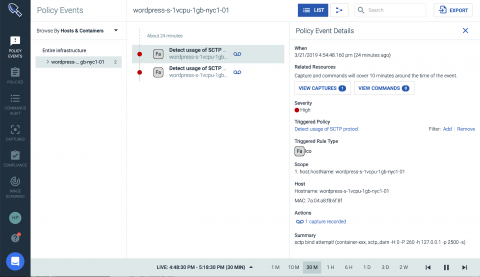
Log management is the answer to all of your digital transformation woes. No, hear me out. At its heart, log management is the (challenging) task of collecting and storing all machine-generated data from across your entire enterprise into a common repository. If this collection doesn’t happen, or if log collection is limited to certain datasets, there’s little chance of deriving those high value insights you dream of.